Computing and Communications Services CIO says a combination of better backend, user awareness making a difference

As October draws to a close, so does Ryerson’s annual cybersecurity awareness month. Brian Lesser, chief information officer of Ryerson’s Computing and Communications Services, said the university is seeing more resilience against attacks like phishing emails, thanks in part to a more robust backend and a growing awareness among students, staff and faculty.
The month-long awareness campaign, which started in the U.S. in 2004, worked out well for the university.
“Students have usually settled in during September and can participate in October more easily than in November or December,” Lesser said.
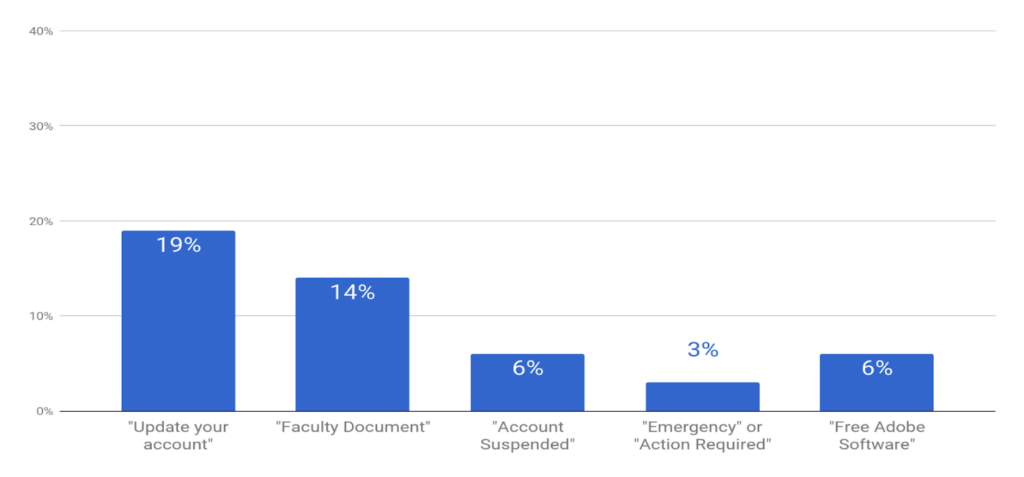
A hallmark of Ryerson’s cybersecurity awareness month are the simulated phishing emails. Phishing is a form of fraud designed to steal confidential information like passwords, or bait victims into sending gift cards or cash. Lesser shared data from 2017 to illustrate how quickly Ryerson students learned to spot the simulations — and hopefully learned not to fall for the real thing. Almost one in five people clicked on phony requests to update their account. By the fourth email — demanding a vague “action required” — those clicks had dropped to three per cent. The hitch? The fifth email, offering free Adobe software, saw the clicks double to six per cent.
Atefeh Mashatan is the director of Ryerson’s Cybersecurity Research Lab at the Ted Rogers School of Management. She might have an explanation for the uptick in clicks for free software: the ‘privacy paradox.’
“The average person will express high valuations of their privacy but when tested in experimentation, they will disclose personal information for a relatively low incentive or reward,” Mashatan said.
Even as knowledge of phishing increased, a free offer might have provided just that low incentive to make users give up their data.
Lesser also attributed a drop in reported phishing attempts to Ryerson permanently retiring the old email system in favour of Google’s G Suite.
“Last year, when we retired the old RMail system, the number of spam/phishing reports we received dropped by 85 per cent,” Lesser said. “And that was just from moving 10 per cent of our RMail email accounts to a Ryerson GMail account.”
Not just students are vulnerable
Phishing attacks don’t just target students. More sophisticated attacks, known as business email compromise attacks, target faculty and staff.
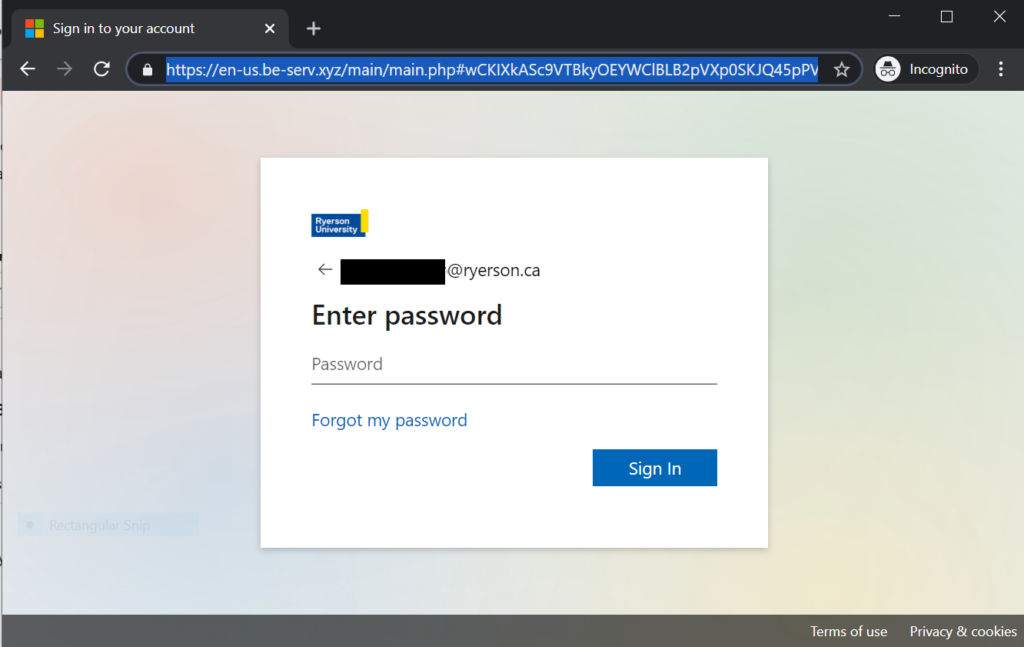
Lesser shared an example of a phishing attempt from a compromised account at another university. It told a Ryerson staff or faculty member (Lesser anonymized the email) to click a link to retrieve an email, and then sent them to a phony login page.
“These emails were sent to executives or people with financial responsibilities at the university,” Lesser said.
Attacks increase even as response drops
Ryerson’s improvements are in stark contrast to the number of attacks, which are increasing.
“Things have gotten worse over the last decade,” Lesser said, noting that it’s difficult to measure just how many phishing attempts are blocked by Ryerson. “Our automated filtering systems block spam and phishing and aren’t all designed to estimate how much of what is blocked is phishing.”
Other attacks, like attempts to crack passwords, are easier to measure.
“We once watched for six days how many guessing attempts we would get if we didn’t rate limit them at our firewalls,” Lesser said. “In six days, we detected 3,641,642 guesses from 3,000-plus machines in 103 countries.”
Lesser said that 94 per cent of those attacks came from outside Canada.
That puts an emphasis on strong, clean passwords, Lesser said. He also recommended haveibeenpwned, a tool that lets users type in their email address and see if it turned up in any website hacks. Those hacks have sometimes exposed users’ passwords as plaintext and been shared online.
As cybersecurity awareness month finishes up, we should all ask if we’ve been pwned.
